F-Secure Scam Kill Chain
A definitive framework for scam tactics and techniques
Over $1 trillion was lost globally to scams in 2023. The internet, with no clear borders, is a hotbed for cyber crime, targeting consumers daily. The cyber threat landscape is overwhelmed with scam tactics, and until now, no framework has comprehensively described how scammers operate. That’s why we created the F-Secure Scam Kill Chain – a detailed breakdown of how modern online scammers operate.¹
A systematic analysis of the scam landscape
At F-Secure, we believe in the power of sharing knowledge. Our goal is to provide a comprehensive understanding of different types of scams. By doing so, we aim to build a rich and detailed knowledge base, breaking down both high-level tactics and more specific techniques. This framework serves as a formal foundation for researching and developing effective defenses against scams. ²
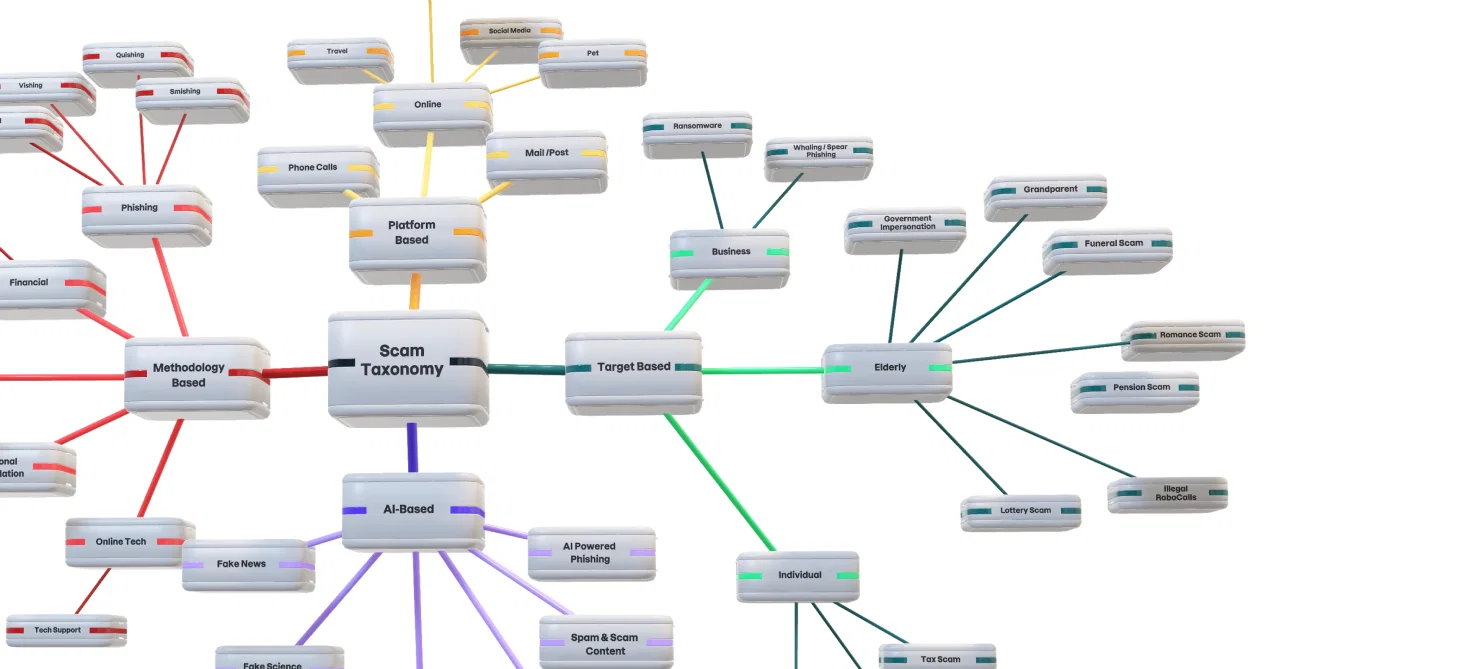
F-Secure Scam Kill Chain
A definitive framework for scam tactics and techniques
1. Reconnaissance and target acquisition | 2. Resource Development | 3. Victim Contact and Engagement | 4. Persistence of Scam | 5. Access and exfiltrate information | 6. Lateral movement | 7. Monetization |
|---|---|---|---|---|---|---|
Goal: Identify potential victims, based on:
| Goal: Build or acquire resources needed to conduct the scam, including:
| Goal: Make contact with victim to deliver bait and engage victim with the bait | Goal: Get the scam to persist for as long as needed | Goal: Get access to any victim information that is needed to complete the scam | Goal: Grow the scam in size | Goal: Turn scam into money |
1.1 Establish target pool based on suitability to scam | 2.1 Acquire infrastructure
| 3.1 Contact and engage victim via email | 4.1 Psychological manipulation of victim
| 5.1 Victim divulges information | 6.1 Promote scam to victim’s contacts | 7.1 Directly transfer funds from victim to scammer |
1.2 Build manual profiles of targets | 2.2 Develop Software
| 3.2 Contact and engage victim via SMS | 4.2 Modify scammer’s virtual presence
| 5.2 Scammer steals victim information by deploying malware | 6.2 Compromise victim’s additional online accounts | 7.2 Indirectly transfer funds from victim |
1.3 Build or acquire target list through automated data collection | 2.3 Acquire services
| 3.3 Contact and engage victim via telephone | 4.3 Change platform used to communicate with victim | 5.3 Scammer gains remote digital access to victim’s device | 6.3 Leverage victim’s access rights | 7.3 Sell victim assets for profit |
1.4 Build or acquire target list from internet databases / sources | 2.4 Acquire personas & accounts
| 3.4 Contact and engage victim via online service controlled by 3rd party | 4.4 Employ malware persistence techniques | 5.4 Scammer accesses victim information via account takeover or digital impersonation | 7.4 Engage victim in investment scheme | |
2.5 Develop the bait
| 3.5 Contact and engage victim via online services controlled by scammer | 4.5 Change victim account information | 5.5 Scammer exfiltrates victim information
| |||
2.6 Improve credibility of the bait
| 4.6 Avoid platform detection or reprisals |
The goal of this phase is to identify potential victims, based on their personal interests, demographics, online accounts, or contact details. Depending on the scam, this could be a very targeted group, or the scammer may cast a wider net to target a whole population based on their proximity to news events, current events, calendar activities, or the like. The techniques vary, but could include manually hunting for victim details from social media (name, address, interests, etc.), performing automatic data collection, or purchasing personal data of victims from closed sources like illegal marketplaces on the internet. At this phase the scammer may also attempt to perform basic psychological profiling, such as looking for people more likely to fall for the given scam.
Goal: Identify potential victims, based on:
Suitability to scam
Availability of data
Personal interests
Demographics
Some scams may require a large potential target population that is likely to be susceptible in some way to the scam. The target pool may be constructed because it is potentially affected by a scam-relevant news item, or because the population lives in a particular timezone, region, or is proximal to a particular scam-relevant event. The target population could also be chosen because they are likely to use a scam-relevant piece of software or platform.
An adversary may manually gather information about potential victims in order to build a targeted profile of them. Personal details, such as victim's contact networks, location, nationality, political inclination, religious beliefs, hobbies, sexual orientation, etc., recent breakups or family tragedies, are used in profiling by adversaries to formulate specific strategies to scam victims. Additionally, scammers may specifically look for victims who have accounts on particular apps, websites, or discussion groups. For example, an online account on a dating website or app indicates that the user is possibly open to a relationship. Similarly, accounts on crypto mining websites indicate interest in cryptocurrency.
To build lists of targets or to acquire personal details of targets, adversaries may perform automated data collection to gather large amounts of raw data, which can then be further filtered and polished to desired granularity. Such automated data collection can be performed on various online resources, each with a different result.
Adversaries may scrape websites or social media sites to acquire personal information about victims. If the scammer already has an existing list of targets, they may scrape websites or social media sites to find additional personal details about them that can be used in the scam. Or, the scammer may use web scraping to generate a list of potential victims. In either case, the end goal is always to get more information about targets of the scam. The data gathered in this phase can also be misused in the later stages of the scam, such as helping the scammer to build fake social media profiles, to create fake product listings on shopping sites, or to apply for loans by impersonating the victim. Data such as photos, videos and voice might also be used to create fake online identities or to create AI-generated content such as voice clones or video deepfakes.
Adversaries may purchase lists of targets or data about targets from special-purpose sources such as illicit marketplaces, people search databases or data brokers, insider-produced lists / “lead generation” services, or public records.
The goal of this phase is to build or acquire resources needed to conduct the scam, including technical infrastructure used to run the scam, as well as the bait used by the scammer to lure the victim. These resources could include physical entities such as computers and human scammers, or it could include virtual resources such as websites, social media accounts, malware, and the like.
Goal: Build or acquire resources needed to conduct the scam, including:
Infrastructure
Software
Services
Personas
Bait
Adversaries may set up, purchase, or steal a variety of technical infrastructure needed to run the scam. Infrastructure may be built for conducting specific scam attacks or it could be generalized for reuse in other scams.
2.1.1. Email infrastructure
Adversaries may require email services for different phases of the scam, for example to send phishing emails. These email services may be purchased, rented, or stolen. Adversaries may also subscribe to SMTP relay services or bulk email services to accomplish the scam.
2.1.2. SMS infrastructure, SMS gateways
If the scam requires SMS contact with victims, an adversary could purchase, rent, or construct an SMS gateway. SMS gateways are used to mass send text messages to phone number(s) at a relatively low price.
2.1.3. Telephone infrastructure
Adversaries may require telephone infrastructure as part of the scam. For example, in order to dial multiple numbers in quick succession, they may need to use robodialers or phone number spoofing technology. Voice-over-IP (VoIP) technology and SIM/eSIM technology can be used to assist with navigation between global telephone providers. For some advanced scams, adversaries may even attempt to spoof a cellular base station in order to intercept communications, using equipment and services often referred to as “SMS Blasters” or IMSI catchers.
2.1.4. Domain services
For scams that require a web domain, adversaries may purchase domains or may employ free-to-use domain names. Adversaries use several techniques to make their domains appear more legitimate: they may compromise existing domains, they may “typosquat” by registering a domain name that resembles a legitimate domain, or they may purchase established domains with lapsed registrations. Adversaries may also employ domain generating algorithms to create and register hundreds of domains at a time. To improve the quality of the scam with HTTPS-enabled connection, adversaries either purchase SSL certificates for the domain names from Certificate Authorities or generate free certificates using services such as Let’s Encrypt. Domains and websites without SSL certificates (i.e. HTTP connections) prompt errors and might not function on modern browsers, so encrypting website connections with HTTPS has become standard for adversaries.
2.1.5. Website hosting
Adversaries use websites to serve malicious content, redirect to other websites, insert forms for stealing information or serve malware. Websites can be hosted on a physical server, cloud-based server or using serverless technologies. Adversaries can also rent servers from bulletproof hosting providers that have lax terms and conditions and refuse takedown requests from international or local law enforcement.
2.1.6. Cloud resources
Adversaries may acquire resources in the cloud to host malicious content. Adversaries may purchase such resources or use or abuse publicly available resources for malicious purposes. For example, adversaries can use Content Delivery Networks (CDNs) or DDoS protection to hide the original IP address of their malicious site or C2 server. File hosting offered by cloud services can be used to host malicious websites. IP Tunneling can be used by adversaries to make a website hosted on computer localhost available to the public internet. The tunneling works by setting up a daemon of, for instance, Cloudflare on the server or computer where the website is hosted and it can be exposed to the internet. They can also exploit misconfigured cloud services for e.g. spamming. Finally, DDoS protection services, such as CloudFlare and similar, can also be used to hide source IP address.
2.1.7 C2 infrastructure
Adversaries may choose to develop and deploy Command and Control (C2) server, or use free-to-use C2 servers developed by other adversaries. Some C2 server capabilities can also be rented or bought. C2 server is used together with malware installation to issue further commands to malware on victim’s device. C2 can also be used to harvest and store victim’s personal information. In the latter example, C2 server can be used as a database or a “dashboard” for accessing and cataloguing stolen information.
Adversaries may need to develop and deploy their own custom software to accomplish the scam.
2.2.1 Custom malware
Adversaries may write custom malware that is deployed as a part of the scam. Some custom malware templates can be obtained for free online. Such malware will conduct malicious activities on the victim’s device such as information stealing, file encryption or destruction for ransoming, and so on. Since custom malware can be quite expensive to create and maintain, this is less commonly used in scams, and when it is, it is usually reserved for high-value targets such as people with large cryptocurrency holdings. For alternatives, see “2.3 Acquire Services.”
2.2.2 OSS project code
Some scams involve malicious custom code deployed into open source software (OSS) repositories or open source libraries used in other software packages. An unsuspecting user will run the code and be infected with malware.
2.2.3 Website and script development
Many scams require a website, whether to provide an interface to collect phishing details or as a shield of legitimacy for a fake company. Website development can include static pages, victim-side scripts that run in the browser, and adversary-side scripts that control the backend functions of the website. Shopping carts, payment software, and chatbot software can also be integrated into websites to give a veneer of legitimacy to the site. When phishing tools are bundled together and sold as a product, they are sometimes called a “phishing kit.” Other website-located malware, such as Magecart attacks, inject malicious code into legitimate websites in order to steal user information.
2.2.4 Custom platform bots
Some scams require victims to interact with malicious bots on instant messaging platforms, websites or social media. These bots can be custom-made, obtained for free online or purchased.
Adversaries might require additional capabilities, resources, or know-how to facilitate the scam.
2.3.1 Acquire Human Personnel
Human personnel are used to scale operations to reach multiple victims. Adversaries can recruit other individuals on online forums and pay them to develop malware, translate text, or conduct social engineering attacks. These groups are loosely affiliated and typically not associated with traditional organized crime families or gangs. However, some large scale scam operations also have been found running in physical locations that resemble call centers. Scammers have been known to staff these locations with both paid labor and forced labor. Operating this type of large-scale “scam center” or “scam compound” is sometimes associated with organized crime groups, since they bring skills in related criminal enterprises such as money laundering and human trafficking.
2.3.2 Acquire XYZ-as-a-Service
Adversaries who lack certain technical expertise can also purchase or rent these services, such as malware-as-a-service or phishing-as-a-service. The ‘XYZ’ here indicates any service that enables the adversary to conduct scams. Such service models allow adversaries to leverage advanced malware and phishing capabilities, while outsourcing the development and maintenance to external developers.
2.4.1 Create or acquire real world identities
To further the scam or obfuscate related criminal activities, adversaries may create fake personas and identities or they may steal other people’s identities. Fake identifications can include fabricated or stolen passports, national ID cards, driving licenses, utility bills, and other documents. Fake identities serve multiple purposes from obscuring identities from victim(s) and law enforcement, to opening financial accounts for monetary transactions or money laundering or setting up shell companies for illegal business use-cases and so on. Fake personal identification might involve creation of new identities using a combination of real and fake data – this is often referred to as ‘Synthetic Identity Fraud’.
2.4.2 Create or acquire online identities or accounts
Depending on the scam, adversaries may require a variety of accounts at various service providers, including online services, social media, sales platforms, payment processors, and the like. In addition to creating entirely new online personas and accounts to further the scam, some adversaries may also steal accounts with established identities, or they may create accounts that impersonate well-known brands, celebrities, or influencers.
2.4.3 Create or acquire financial service accounts
In order to pay for services related to the scam or to plan for eventual monetization of the scam, an adversary may need to set up accounts to handle financial transactions. Brick-and-mortar banks, online-only banks, peer-to-peer (P2P) payment services, and cryptocurrency exchange accounts are all options for transferring funds, but different companies can have different expectations for how much customer legitimacy is required. Traditional, legitimate banks typically follow “Know Your Customer” laws, which require documentation of a customer’s identity. They also place strict limits on how much money can be moved without triggering alerts. However, adversaries might still leverage traditional bank accounts for criminal activities, particularly when the scam involves a money launderer or “money mule” participating in the scam. Online banks, sometimes referred to as “neobanks” or “digital banks”, operate fully online with no physical bank locations, which might make it easier for adversaries in some situations to skirt around rules and regulations, use fraudulent identification, and the like. Peer-to-peer payment services can facilitate easy transfer of funds between victim and scammer, and in some instances the services might lack fraud protection and investigatory power of traditional banks and credit card companies. Cryptocurrency exchanges can assist a scammer in moving money between virtual and fiat currency, but can vary widely in their level of adherence to regulatory requirements about identification and fraud prevention.
As part of the scam, the adversary sometimes will create “bait” that is sent to the victims to act on. Whether the bait takes the form of an email, message, advertisement, or some other artifact, it needs to be crafted carefully so that the victim engages with it.
2.5.1 Create Bait Email or SMS Message
Emails and SMS messages are both common delivery methods for scam bait. Emails have an advantage in that consumers already receive many legitimate emails from businesses, and there are fewer length and content issues than with SMS. However, SMS messages have a high open rate, making it likely the potential victim could actually engage with the message. Scammers can purchase phishing kits to help them craft effective email and SMS messages.
2.5.2 Create Bait Website
For some scams, adversaries will build a fake website designed to covertly extract users’ personal or financial information. Other websites will be designed to give an air of legitimacy to a scam, such as with a fake shopping website or product review scam. Adversaries may create such websites manually or may use phishing kits to automate the development process.
2.5.3 Create Bait Advertisement
Adversaries may purchase online advertisements that have been produced specifically for scamming victims, or they may build their own advertisements. Potential victims will sometimes see scam ads as sponsored search engine results, or the ads might be delivered personally to victims via social media profiles or popular messenger services.
2.5.4 Create Bait Product Reviews, Likes, Engagement
Adversaries may purchase fake reviews, stars, subscriptions, and likes.
2.5.5 Create Bait Posts
Scammers can create fake social media or platform posts in order to boost the likelihood of more potential victims seeing the bait, or in order to spread malicious links.
2.5.6 Create Bait Mobile App
Adversaries may create fake apps for popular mobile platforms. These apps may carry out a variety of tasks such as providing fake functionality, stealing information, etc. As part of scam campaigns, adversaries may target victims using their smartphones, enticing them to install such scam apps and further continue with the scam attack. A quick way for scammers to build such mobile apps is to copy real apps and add malicious code.
The better the quality of the bait, the more likely it will be that the potential victim will engage with it. The adversary can use AI or other techniques to create more realistic scam bait.
2.6.1 Improve Bait with AI
Scammers use artificial intelligence to create convincing images and texts. They also use it to create voice clones and video deepfakes. All of these improvements lend additional credibility and authenticity to the scam bait.
2.6.2 Improve Quality of Brand Impersonation
When impersonating a brand, whether in a phishing email, an advertisement, or a fake website, scammers have figured out different techniques to create copycat content that closely resemble the originals.
2.6.3 Mask Suspicious URLs
In order to hide suspicious URLs from the potential victim, an adversary may generate a QR code or use a URL shortening service.
2.6.4 Leverage SEO Poisoning
Adversaries may create content that tries to manipulate search engine rankings so that their malicious content appears among the top results.
2.6.5 Write social engineering scripts
Scammers will often write social engineering scripts that they can use when interacting with victims over the telephone or on other platforms. By having a pre-planned, professional-sounding script, the scammer can design a process that is fool-proof and easily replicable. The script can then be used by multiple people working as a group or as part of a scam call center.
The goal of this phase is to make contact with the victim in order to deliver the bait and to further engage victim with the scam.
Goal: Make contact with victim to deliver bait and engage victim with the bait
Adversaries may send malicious links directly in email to the potential victim, or they may also include email attachments containing malicious links, malware, fake invoices, and the like.
Adversaries may send phishing SMS messages that trick users into starting a conversation or that contain malicious links. Phishing SMSs use the same tactics as in emails, with the exception that they tend to be more concise.
Adversaries may make fake calls to victims, or some scams have the victims call the adversary. Phone calls happen in real-time, and can convey a sense of trust, urgency, or danger, which may not be possible via other techniques.
Adversaries might contact victims directly via social media or instant messaging platforms. The potential lures used on such platforms include fake celebrity endorsements, fake product offers, fake job interview calls, fake lottery winnings, etc. For some scams, such as romance scams and investment scams, the adversary may target victims and make initial contact with them on a specialty site such as an online dating platform or cryptocurrency enthusiast website.
In some scenarios, the scammer does not reach out directly to the potential victim. Instead, the victim finds the scammer’s malicious website or app through other means such as targeted advertising, links in comments sections of a website, or by lookalike web domains or lookalike app names.
The goal in this phase is to ensure that the scam is able to be completed. The scammer will employ various techniques to persist the scam for as long as is necessary.
Goal: Get the scam to persist for as long as needed
Whether scams involve direct or indirect contact, the scammer may employ a variety of psychological manipulation techniques on the victim in order to get them to comply.
4.1.1 Assert authority
4.1.2 Employ likeability, seduction
4.1.3 Create scarcity, urgency
4.1.4. Exploit victim’s shame
4.1.5 Build peer pressure, social validation
4.1.6 Leverage gradual commitment, positive reinforcement
4.1.7 Create obligation or reciprocity
In order to persist the scam, the scammer may delete, change, or add new scam personas or online presences. This can include introducing new characters into the scam, removing online comments, advertisements, taking down malicious websites, and so on.
Another technique to keep the scam going as long as possible is to convince the victims to move conversations to a different messenger under the pretext of greater safety and security.
For scams that are malware-based, the scammer may employ common techniques for extending the life of the malware and avoiding detection by the victim.
For an account-based scam, one of the first things a scammer will do when they get access to a victim’s account information is to change password and password recovery details for the account. This ensures that they will have a longer amount of time to work with the account to accomplish their scam. They may also change contact details, change account recovery options, and enable or change multi-factor authentication (MFA) settings on the account.
Shopping scammers will often use fake tracking numbers in order to buy themselves time with a victim who has not received a package. Tracking number fraud also allows the scam seller to claim innocence when their victim reports the transaction as “Item Not Received.” Scammers can generate fake tracking numbers, or they might re-use tracking numbers from a prior delivery, or they might ship a low-cost, low-weight item so they can claim that the package did arrive.
The goal of this phase of the scam is to get access to any victim information that is needed to complete the scam. The information a scammer is seeking can take many forms, and the scammer may need multiple kinds of information in a single scam.
Goal: Get access to any victim information that is needed to complete the scam
In this technique, adversaries lure or deceive the victims into sharing their own sensitive information.
In this technique, the adversary deploys malware onto a victim’s device to steal information.
Here the adversary uses screen sharing software or a remote access tool to access the victim’s device.
An adversary may attempt recovery of accounts using compromised information, or may impersonate the victim’s devices. One technique is SIM card swapping, wherein the adversary orders a new SIM card with the victim’s details, thus giving the scammer control over the victim’s phone number.
The adversary may exfiltrate data from the victim by simply downloading it, by syncing the victim’s cloud storage data, by setting an email forwarder, or by leveraging command-and-control (C2) infrastructure.
5.5.1 Exfiltrate victim information with C2 channel
In this technique, adversaries establish a channel with a command-and-control (C2) server either by using existing resources or building their own server from scratch. The data acquired from the victim is sent to such a C2 server either in plaintext, archived, or encrypted and archived form. The C2 channel can be custom or could use a publicly available service (such as Google Drive, Amazon, etc.) for hosting. Using a publicly available service provides the adversary with an advantage of hiding in plain sight.
5.5.2 Exfiltrate victim information using a chat or messaging service
Messaging and communication platforms such as Telegram or Discord have easy-to-operate bot APIs and are often misused by adversaries to become C2 servers to exfiltrate and store sensitive data.
5.5.3 Exfiltrate victim information using email forwarders
5.5.4 Exfiltrate victim information to cloud services
The goal of this phase is to grow the scam in size, either in number of victims or potential value of information gained.
Goal: Grow the scam in size
The adversary may promote the scam using the victim’s email contacts, SMS contacts, or social media contacts, sometimes impersonating the victim to make contact with these new potential victims. The scammer may also use the victim’s identity to create social media posts, comments, and direct messages to promote the scam and find additional victims.
The adversary may attempt to gain additional leverage by compromising the victim’s other accounts. To do this, the scammer may attempt password resets, password stuffing (using the credentials of one service on another service), or compromising the victim’s Single-Sign-On (SSO) privileges.
The scammer will attempt to gain elevated privileges, for example by accessing the victim’s administrator or employee privileges, in order to spread the scam to other accounts, to gain additional information from the victim, or to find additional victims.
The goal of this phase of the scam is to turn data or access into money.
Goal: Turn scam into money
In some scame, it may be possible for the adversary to gain funds directly from the victim, in the form of a credit card payment, bank transfer, cryptocurrency payment, peer-to-peer payment service transaction.
Some scams require an indirect monetization scheme, in which the adversary indirectly extracts funds from the victim. For example, the scammer might clone the victim’s credit card in order to make purchases or withdraw cash, or the scammer might force the victim to buy gift cards which the scammer can convert to cash.
An even more indirect method of monetization might involve the scammer attempting to profit from the victim's assets or information. For example, the adversary could steal the victim’s identity to take out bank loans. The adversary could sell the victim’s stolen data or other assets, including physical or virtual property. The scammer might also use victim resources for cryptocurrency mining.
The adversary could get money from a victim as part of one or more shady investment schemes.
Rug pulls, exit scams, and pump and dump schemes are all types of fraud in which perpetrators disappear with a victim’s funds—whether by draining a crypto project's liquidity (rug pull), shutting down a business without delivering promised goods/services (exit scam), or artificially inflating an asset's price through false promotion before selling at the peak (pump and dump).
A Ponzi scheme is a fraudulent investment operation that pays returns to existing investors using capital from new investors rather than from legitimate business profits, inevitably collapsing when new recruits become insufficient.
A pyramid scheme is a business model that recruits members with promises of payments for enrolling others into the scheme rather than from selling legitimate products, creating an unsustainable structure that enriches early participants at the expense of later ones.
Fake cryptocurrency trading platforms are apps that purport to help “investors” make profits in online trades. The apps show the victim graphs and balance sheets indicating that they have earned profits, but the balances and graphs that the victim sees are fake. Once the victim tries to withdraw their "gains", the scammer disappears with all the money and the app becomes inaccessible.
Copyright F-Secure Corporation 2025. All rights reserved.
Effortlessly protect consumers from scams
The online scam landscape is extensive, making it challenging to anticipate and protect your customers from every potential threat. Partnering with F-Secure means you don’t have to face these challenges alone – our advanced scam protection technology works behind the scenes to mitigate the most prevalent online threats facing your consumers today.Flexible integration options
Sources
¹ GASA The Global State of Scams 2023
² Inspired by the MITRE ATT&CK® framework, developed by the MITRE Corporation