Trojan:SymbOS/Onehop.A
Summary
Trojan:SymbOS/Onehop.A causes the infected device to reboot when trying to use system applications.
Removal
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Onehop.A also uses a modified Bluetooth-Worm:SymbOS/Cabir malware to distribute copies of Trojan:SymbOS/Bootton.A to the first Bluetooth-reachable device it finds.
Onehop.A is distributed in a malicious SIS file named 'PhotoID.v3.06_NEW_7610_3230_6630_SMPDA.sis'.
If a device is infected with Onehop.A, pressing menu button or any system application button the device immediately reboots. Only calling and answering calls works. All functions which need some system application, such as SMS and MMS messaging, web browsing and camera no longer function.
Like Skulls.A the Onehop.A replaces the application icons with it's own icon, this time the icon is a heart icon with the text "I-Love-U"

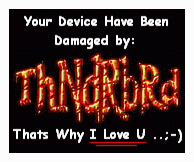
This trojan contains this message:
Saying HELLO From Here (SYRIA) TO All The WORLD !!! I Wish U N-Joy UR Damaged Device .. U Know, Not all may Read These Words But, No Problem Bcuz Some will, But even This, Thats The Way I Love U All ...;-) Regards, ThNdRbRd
And this hidden image:
Onehop.A also installs a modified version of Bluetooth-Worm:SymbOS/Cabir that it uses to spread Trojan:SymbOS/Bootton.A, though the Cabir worm is not started automatically - it will only start when the device boots.
Execution
In its structure Onehop.A is quite similar to the Trojan:SymbOS/Skulls family, with the exception that instead of replacing system files with corrupted binaries, Onehop.A uses application that causes device to reboot.
On execution, the trojan installs a small component that resets the device if executed. This component is installed into locations where it replaces system and third party applications. Onehop.A disables most of critical system functions and third party file managers, so that even if the device wouldn't immediately reboot it is still unusable before it is disinfected.
In addition of disabling applications on the phone, uses a modified version of Cabir as a distribution component for SymbOS/Bootton.A. Instead of sending a copy of itself (normally generated at startup), the modified Cabir loads the SIS file installed by Onehop.A into a location where Cabir expects to find its own SIS file; the worm then starts sending the replaced file as per its normal routine.
The modified Cabir is based on Cabir.B and contains the same replication routine flaw - it is only capable of sending SymbOS/Bootton.A to the first phone it finds after reboot. The targeted phone receives Bootton.A over Bluetooth only if the user accepts connection.
The modified Cabir that Onehop.A infects the device with is incapable of spreading, so it is detected as component of Onehop.A, not as separate malware.