Email-Worm:W32/Bagle.C
Summary
This type of worm is embedded in an email attachment, and spreads using the infected computer's emailing networks.
Removal
For removal instructions specific to Bagle infections, see Email-Worm:W32/Bagle.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Email-Worm:W32/Bagle.C distributes copies of itself as file attachments to email messages that use differing subject lines. Once executed, the worm functions as a backdoor and disables certain security software.
Bagle.C was first found in the wild in the early morning of February 28th, 2004. This variant was programmed to stop spreading after March 14th, 2004.
Infection
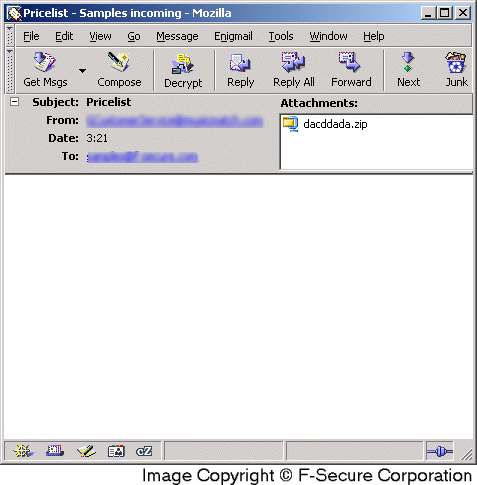
Email-Worm:W32/Bagle.C arrives as a zipped EXE file attachment to email messages that use differing subject lines. The attachment uses the icon of a Microsoft Excel spreadsheet file as a decoy:

On initial execution, the worm starts the Windows Notepad (notepad.exe) to conceal its activity. It then drops several files to the Windows System Directory:
- %SysDir%\readme.exe - dropper of other components
- %SysDir%\onde.exe - main worm body
- %SysDir%\doc.exe - external library helper
'Readme.exe' is added to the registry as
- [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\gouday.exe]
to ensure that the worm will be activated when Windows starts. To indicate whether the worm was run for the first time it creates another value in the registry as
- [HKCU\Software\DateTime2\frun]
Activity
Bagle.C comes with a backdoor that listens on a TCP port 2745, which is hardcoded in the worm's body. The backdoor provides full remote access to the infected computer. It can be used to download and execute arbitrary programs from the Internet. When the worm is started it connects to a list of predefined web servers and tries to access a PHP file with certain parameters. One of the parameters is the TCP port where the backdoor is listening which suggests that this functionality is used to collect the addresses of infected computers. The payload of Bagle.C contains a thread that terminates processes with the following names:
- ATUPDATER.EXE
- AVWUPD32.EXE
- AVPUPD.EXE
- LUALL.EXE
- DRWEBUPW.EXE
- ICSSUPPNT.EXE
- ICSUPP95.EXE
- UPDATE.EXE
- NUPGRADE.EXE
- ATUPDATER.EXE
- AUPDATE.EXE
- AUTODOWN.EXE
- AUTOTRACE.EXE
- AUTOUPDATE.EXE
- AVXQUAR.EXE
- CFIAUDIT.EXE
- MCUPDATE.EXE
- NUPGRADE.EXE
- OUTPOST.EXE
- AVLTMAIN.EXE
Propagation (email)
Bagle.C recursively searches all drives on the infected computer to locate file that could contain email addresses. It parses these files and collects all email addresses it can find. Files with the following extensions are checked:
- .wab
- .txt
- .htm
- .html
- .dbx
- .mdx
- .eml
- .nch
- .mmf
- .ods
- .cfg
- .asp
- .php
- .pl
- .adb
- .sht
The mailer routine will ignore all the addresses that contain the any of these strings:
- .ch
- @hotmail.com
- @msn.com
- @microsoft
- @avp.
- noreply
- local
- root@
- postmaster@
Using its own SMTP engine Bagle sends messages with infected attachments to the collected addresses. The SMTP engine uses direct Mail eXchange (MX) lookup on the target domain so it does not depend on email settings of the infected computer. The body of the messages is empty. The sender address in the email is spoofed. The infected emails can have the following subjects:
- New Price-list
- Hardware devices price-list
- Weekly activity report
- Daily activity report
- Maria
- Jenny
- Jessica
- Registration confirmation
- USA government abolishes the capital punishment
- Freedom for everyone
- Flayers among us
- From Hair-cutter
- Melissa
- Camila
- Price-list
- Pricelist
- Price list
- Hello my friend
- Hi!
- Well...
- Greet the day
- The account
- Looking for the report
- You really love me? he he
- You are dismissed
- Accounts department
- From me
- Monthly incomings summary
- The summary
- Proclivity to servitude
- Ahtung!
- The employee
The attachment is a ZIP file with random name which is up to eight characters long and made up of the letters 'a' 'b' and 'c'.