Worm:W32/CodeRed.F
Summary
CodeRed.F is almost identical to CodeRed II, with just two bytes changed. CodeRed II stopped spreading in in the end of 2002 - the change in CodeRed.F changes this and enables it to spread forever.
Removal
Disinfection instructions specific to each variant of the CodeRed worm are provided in the Technical Details section below.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Variant:CodeRed F
Worm:W32/CodeRed.F was found spreading in the wild from March 11th, 2003, or more than 18 months after the original CodeRed worm spread across the world faster than any worm before it.
Just like CodeRed II, this worm will install a backdoor to infected web server, enabling any web surfer to easily execute commands on the server by just typing them in a special URL. However, since CodeRed.F still uses the old exploit to infect IIS Web Servers, the number of vulnerable machines is not too high. Most of them are forgotten web servers or home machines without firewall.
This variant will reinfect unprotected IIS Web servers, most of which were already infected earlier by CodeRed II. We're not expecting this to become as big as it was in 2001.
CodeRed.F is almost identical to CodeRed II, with just two bytes changed. CodeRed II stopped spreading in in the end of 2002 - the change in CodeRed.F changes this and enables it to spread forever. Just like CodeRed II, this worm will install a backdoor to infected web server, enabling any web surfer to easily execute commands on the server by just typing them in a special URL.
Removal instructions
Microsoft has shipped a tool to eliminate the obvious damage caused by CodeRed II worm. This tool can be downloaded from: http://download.microsoft.com/download/iis50/Tool/1.0/NT45/EN-US/CodeRedCleanup.exe. More information on the tool from Microsoft site: http://www.microsoft.com/technet/itsolutions/security/tools/redfix.asp
Variant:CodeRed II
Third variant of the Code Red worm has been spreading in the wild since August 4th, 2001. It targets Microsoft IIS www servers, and does not pose a threat to end users. CodeRed II is a rewritten version of the original Code Red worm. It uses the same IIS hole to gain access on the web server and then continues to find new vulnerable systems.
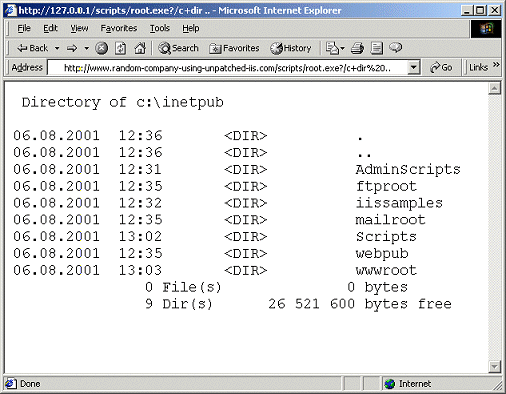
Interestingly, Code Red II has been programmed to spread more aggressively in China than anywhere else. This might be in relation to the Chinese references in the original worm. The most important feature of Code Red II is that it installs a backdoor into systems it infects. This is accomplished by copying the standard Windows NT/2000 command interpreter "cmd.exe" into web server's "scripts" directory. As a result, any web surfer can now execute commands on any infected www site just by typing suitable URLs to the web location. Below, a 'DIR' directory listing command has been executed.
Technical details
When a host gets infected it starts to scan for other hosts to infect. It probes random IP addresses but the code is designed so that probing of neighbour hosts is more probable. If the infected system has the language set to Chinese the worm starts more aggressive scanning (600 threads instead of 300). The scanning runs for 24 hours after the infection (48 for Chinese machines) and then the system is rebooted. There is a time limit in the code that will stop the worm on the 1st of October. At that time it will reboot the machine and stop spreading. The installed trojan still remains in the system! The worm drops a trojan program to '\explorer.exe' that modifies different some IIS settings to allow a remote attack of the infected host.
The standard command interpreter 'cmd.exe' is copied to '\inetpub\scripts\root.exe' and to '\progra~1\common~1\system\MSADC\root.exe'. The worm creates these files to both 'C:' and 'D:' drives if they exist. These copies of the 'cmd.exe' will allow any attacker to execute commands on the remote system really easily.
Trojan part of the code
First of all it disables the System File Checker (SFC) functionality in Windows. SFC is responsible for checking the integrity of system files. Two new root directories are added to the IIS configuration: '/c' that points to 'c:\' and '/d' that points to 'd:\'. This makes sure that even if the copies of 'cmd.exe' the worm made are removed the system can still be compromised.
Modifications to the registry:
'SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SFCDisable' is set to 0xffffff9d that disables the System File Checker.
',217' is appended to these keys:
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\Scripts'
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\MSADC'
These keys make 'C:' and 'D:' accessible trough the webserver:
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\C'
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\C'
Removal instructions
First apply the necessary security patches from Microsoft:
- http://www.microsoft.com/technet/security/bulletin/ms01-033.asp
- http://www.microsoft.com/technet/security/bulletin/MS00-052.asp
The first one fixes the vulnerability the worm uses to spread. The second one fixes the problem that makes Windows to run the trojanized 'explorer.exe' from the root folder. Both patches must be applied. When the patches are applied the system has to be rebooted to eliminate the worm itself if it was still active. The following files must be deleted:
- '\inetpub\scripts\root.exe'
- '\progra~1\common~1\system\MSADC\root.exe'
- '\explorer.exe'
These keys have to be removed:
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\C'
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\D'
The added ',217' string has to be removed from these keys:
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\Scripts'
- 'SYSTEM\CurrentControlSet\Services\W3SVC\Parameters\Virtual Roots\MSADC'
A tool to perform the forementioned actions is available at:
- ftp://ftp.f-secure.com/anti-virus/tools/f-codered.zip
Optionally, the contents can be downloaded from:
- ftp://ftp.f-secure.com/anti-virus/tools/f-codered.exe
- ftp://ftp.f-secure.com/anti-virus/tools/f-codered.txt
The backdoor components that the worm drops into infected system are detected by F-Secure Anti-Virus with updates released at August 5th, 2001.
Variant:CodeRed.A
This is original Code Red web worm, found originally in July 2001.
UPDATE ON 1ST OF AUGUST, 2001 By 15:00 GMT,
15 hours after widespread Code Red infections restarted, the situation is getting rapidly worse. The worm has gone worldwide again, infecting vulnerable web sites at an increasing rate. The number of infected servers almost doubles every hour, and has passed 20,000 infected machines. On comparison, on 19th of July, Code Red infected around 300,000 servers, and was only stopped because the worm stopped infections by itself. This time around the worm won't stop spreading for another three weeks.
UPDATE ON 1ST OF AUGUST, 2001 By 12:00 GMT,
12 hours after the new spreading phase for the Code Red worm restarted, no visible effects of the worm could be seen. The worm did restart spreading, as feared, but initial rate of infections was not very fast. The worm might gain more ground later on, but it's likely that the number of reinfected web servers will be lower than in July, and effects of the worm to general public will be minimal.
Basic information on the Code Red worm
Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread. When it infects a server it starts to scan for other vulnerable servers and infects them. During a certain period of time the worm only spreads, then it initiates a Denial-of-Service (DoS) attack against www1.whitehouse.gov and finally suspends all the activities.
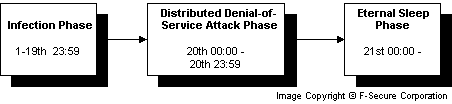
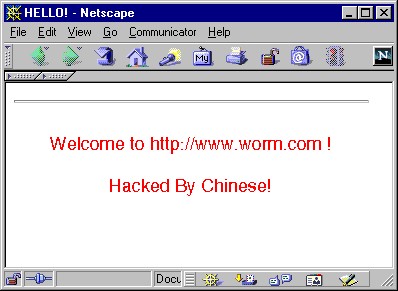
This repeats every month. The time zone in the above picture is GMT. The worm can resume into infection phase at midnight July 31st, if there is infected servers in the Internet with incorrect date settings causing that they already are scanning for vulnerable hosts; or the worm is restarted manually by a malicious party. The front page of an infected server might have been changed by the worm to following:
Removal instructions
Apply the security patch for this vulnerability from http://www.microsoft.com/technet/security/bulletin/ms01-033.asp. Then reboot the server. Since the worm's code is not written to a hard disk (it exists only in memory) rebooting will eliminate the infection completely.