Rogue:W32/Renos
Summary
Dishonest antivirus software which tricks users into buying or installing it, usually by infecting a user's computer, or by pretending the computer is infected.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
In certain circumstances, F-Secure Anti-Virus may not be able to automatically remove files; the user must manually select the correct disinfection action before the antivirus program will proceed.
If a file detected as not-virus:Hoax.Win32.Renos is an executable with a DLL or EXE extension, and is located in Windows, Windows System or in a root folder of C: drive, this file can be safely deleted or renamed.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Rogue:W32/Renos is program that displays annoying fake security warnings. The aim of this software is to trick a computer user to download third-party cleaning utilities, usually anti-spyware scanners.
Installation
The Renos executable file is usually dropped by malicious websites onto the computer system. It may also be delivered in the payload of a trojan.
Typically when a Renos' executable file is run, it drops a DLL file into Windows System folder and registers it as a system component. The DLL is the main Renos component.
Activity
When active, Renos shows a blinking icon in System Tray and periodically (actually quite often to be annoying) shows a fake security warning:
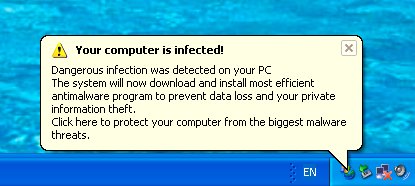
When a user clicks on this alert, his web browser is redirected to a website that offers a cleaning utility (usually anti-adware) for download.