Naco.E
Summary
Naco.E worm was found late on June 2nd, 2003. It spreads via email and peer-to-peer networks. It also tries to steal or delete user's data. Additionally the worm has backdoor capabilities. The worm arrives in emails which subject, body text and attachment name vary.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm's file is a PE executable 32768 bytes long, compressed with UPX file compressor. The uncompressed worm's file size is over 100 kilobytes. The worm has a backdoor (hacker's remote access tool) routine, can perform a DoS (Denial of Service) attack on certain servers, can destroy data on a hard drive.
Installation to system
To infect a system, the worm's file should be run by a user. When the worm's file is run, it copies itself to Windows System directory with ANACON32.EXE name and creates a startup keys for this file in System Registry:
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run] "ALM" = "[path to worm's file] [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] "Under20" = "[path to worm's file] [HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Run] "Under20" = "[path to worm's file] [HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices] "Services" = "[path to worm's file]
As a result of such actions, the worm's file will be loaded every time Windows starts.
Spreading in emails
The worm spreads itself as an attachment to email messages that it composes from its internal text strings.
The subject of an infected message can be one of the following:
Out of my heart? Nelly Furtado! New! Dragon Ball Fx TIPs: HOW TO DEFACE A WEBSERVER? What New in The ScreenSaver! FoxNews Reporter: There are no Solution for SARS? Get Your Free XXX Password! Gotcha baby! Crack for Nokia LogoManager 1.3 Help me plz? TechTV: New Anti Virus Software News: US Goverment try to make wars with Tehran. Re: are you married?(3) Seagate Baracuda 80GB for $??? Small And Destrucive! Alert! New Variant Anacon.D has been detected! Free SMS Via NACO SMS! Patch for Microsoft Windows XP 64bit Your FTP Password: iuahdf7d8hf Get Free SMTP Server at Click Here!
The body of an infected message can be:
Hello dear, I'm gonna missed you babe, hope we can see again! In Love, Rekcahlem ~ ~ Anacon
or
Hi babe, Still missing me! I have send to you a special gift I made it my own. Just for you. Check it out the attachment. Your Love, Rekcahlem
or
Great to see you again babe! This is file you want las week. Please don't distribute it to other. Regard, V.C.
or
Attention! Please do not eat pork! The SARS virus may come from the pig. So becareful. For more information check the attachment. Regard, WTO
or
(blank) You may not see the message because the message has been convert to the attachment. Please open an attachment to see the message.
The attachment name of an infected message is usually ANACON32.EXE, however we recived a few infected messages with attachments named NACO.EXE and with some other names, that are not listed in the worm's code.
Here's an example of how an infected message looks like:
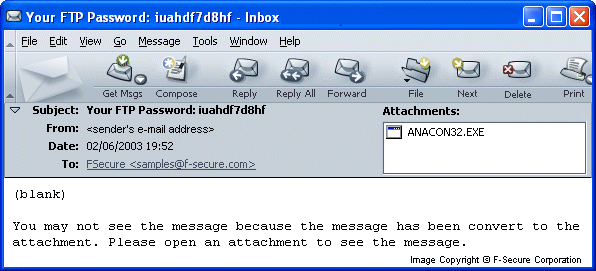
Spreading in P2P (peer-to-peer) networks
The worm tries to locate shared folders of popular file sharing clients - Kazaa and Grokster and copies itself to these folders with the following names:
The Lost Jungle.mpg.exe The Matrix Reloaded Trailer.jpg.exe Replacement Killer 2.avi.exe Trailer DOOM III.exe WinZip9Beta.exe WhatIsGoingOn.exe NokiaPolyPhonic.exe TNT.exe Dont Eat Pork SARS in there.exe About SARS Solution.doc.exe TIPS HOW TO CRACK SYMANTEC SERVER.txt.exe VISE MINDVISION.exe Uninstal.exe WindowsSecurity Patch.exe Hide Your Mount.exe Patch - jdbgmgr.exe NEW POWERTOY FOR WINXP.exe Generate a Random PAssword.exe OfficeXP.exe Ripley Believe It Or Not.exe Anacon The Great.exe New Variant.exe SMTP OCX.exe DialUp.pif Lost YourPassword.txt.exe Hack In 5 Minute.exe Get Lost.exe Oh Yeah Babe.exe Sucker.exe MSWINSCK.OCX.EXE Downloader.exe HeavyMetal.mp3.exe JackAndGinnie.exe RosalindaAyamor fxanacon.com GetMorePower.exe Hacker HandBook.exe Dincracker eZine.exe La Intrusa.exe Porta.exe
When someone downloads and runs any of these files, he/she becomes infected with the worm and it starts to spread further from a newly-infected computer.
Payload
The worm can kill tasks of certain anti-virus, security and other software and delete their files. The following software is affected:
Zonealarm.exe Wfindv32.exe Webscanx.exe Vsstat.exe Vshwin32.exe Vsecomr.exe Vscan40.exe Vettray.exe Vet95.exe Tds2-Nt.exe Tds2-98.exe Tca.exe Tbscan.exe Sweep95.exe Sphinx.exe Smc.exe Serv95.exe Scrscan.exe Scanpm.exe Scan95.exe Scan32.exe Safeweb.exe Regedit.exe Rescue.exe Rav7win.exe Rav7.exe Persfw.exe Pcfwallicon.exe Pccwin98.exe Pavw.exe Pavsched.exe Pavcl.exe Padmin.exe Outpost.exe Nvc95.exe Nupgrade.exe Normist.exe Nmain.exe Nisum.exe Navwnt.exe Navw32.exe Navnt.exe Navlu32.exe Navapw32.exe N32scanw.exe Mpftray.exe Moolive.exe Luall.exe Lookout.exe Lockdown2000.exe Jedi.exe Iomon98.exe Iface.exe Icsuppnt.exe Icsupp95.exe Icmon.exe Icloadnt.exe Icload95.exe Ibmavsp.exe Ibmasn.exe Iamserv.exe Iamapp.exe Frw.exe Fprot.exe Fp-Win.exe Findviru.exe f-Stopw.exe f-Prot95.exe f-Prot.exe f-Agnt95.exe Espwatch.exe Esafe.exe Ecengine.exe Dvp95_0.exe Dvp95.exe Cleaner3.exe Cleaner.exe Claw95cf.exe Claw95.exe Cfinet32.exe Cfinet.exe Cfiaudit.exe Cfiadmin.exe Blackice.exe Blackd.exe Avwupd32.exe Avwin95.exe Avsched32.exe Avpupd.exe Avptc32.exe Avpm.exe Avpdos32.exe Avpcc.exe Avp32.exe Avp.exe Avnt.exe Avkserv.exe Avgctrl.exe Ave32.exe Avconsol.exe Autodown.exe Apvxdwin.exe Anti-Trojan.exe Ackwin32.exe _Avpm.exe _Avpcc.exe _Avp32.exe
The worm also stops Norton Anti-Virus Auto Protect Service, deletes files in C:\SafeWeb\ folder and destroys Trojan Defense Suit software.
On 1st, 4th, 8th, 12th, 16th, 20th, 24th and 28th day of a month the worm can delete all files on C: drive, in Windows and Windows System directory and it can also format D: drive.
When the payload is activated, the worm displays a messagebox:
Anacon III I miss you babe... W32.Anacon.D@mm
Additionally the worm tries to share infected computer's hard drives, so they become accessible from Internet.
Defacing websites
If a worm discovers an IIS server on an infected computer, it deletes all .HTM, .HTML and .ASP files in the \Inetpub\wwwroot\ folder (root folder of a webserver) and creates several files there:
index.htm default.htm index.html default.html index.asp default.asp
These files contain the following message that will be displayed if anyone connects to a webserver located on an infected computer:
WARNING! YOUR WEB SERVER HAS BEEN HACKED BY ANACON MELHACKER. Anacon G0t ya! By Melhacker - dA r34L #4(k3R!
DoS Attack
The worm can perform a Denial of Service (DoS) attack on the following servers:
212.143.236.4 (Israel Ministry of Foreign Affairs) 62.154.244.36 209.61.182.140 (Israel.com) 198.65.148.153 (Arutz Sheva - Israel National News) 212.150.63.115 208.40.175.222 (Jewish Virtual Library) 161.58.232.244 161.58.197.155 (Israel Travel and Hotels Guide) 194.90.114.5 (United States embassy in Israel)
Backdoor
The worm has backdoor capabilities. The worm listens to commands from remote computer. A hacker from a remote computer can perform the following actions on an infected computer:
- start/stop keylogger (records user's keystrokes) - get and change display settings (resolution, wallpaper) - restart or hang an infected computer - get information about an infected computer - get cached passwords - get information about the backdoor - get process list and terminate processes - play media files - open/close CD-ROM tray - show/hide Task Bar - change keyboard settings (enable/disable CTRL+ALT+DEL) - remove backdoor - enable/disable clipboard - change mouse settings (enable/disable doubleclicking) - display a messagebox
The stolen information is sent to 'chatza@phreaker.net' email address via 'smtp.phreaker.net' server.