Technical Details
Unlike most Commwarrior variants, Commwarrior.Q is a recompiled version that contains new functionality. Like Commwarrior.C, Commwarrior.Q spreads via Bluetooth, MMS messages, and to any memory card that is inserted into the infected phone. Unlike Commwarrior.C, Commwarrior.Q will also search for any SIS files in the phone or memory card and will infect those SIS files with itself.
Infection
Commwarrior.Q affects only Symbian Series 60 phones that use Symbian OS version 8.1 or older. This means that the latest model of phones that will be affected is the Nokia N72. Phones using Symbian OS 9.0, such as the Nokia E70 or 3250, will not be affected.
The worm is delivered in an infected SIS file, which have only the Commwarrior executable component.
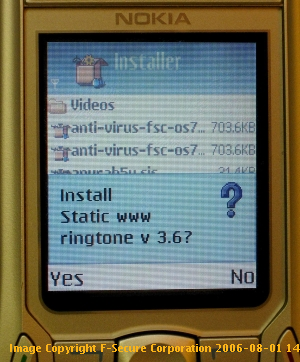
Unlike previous variants of Commwarrior, Commwarrior.Q does not use a static product name that is shown during installation.
Previous variants always showed the same name, thus making them easy to identify. Commwarrior.Q instead contains an internal list of strings that is used to generate random, but plausible looking filenames.
The user is prompted to install the SIS file, as can be seen in the screenshot below:
Installation
When the SIS file is installed, it will drop the its executable with a random name, for example 5k8jb1fo.exe, either into C:\ or to a directory that has a random name such as C:\uqxo5dh7xtyc5.
When the Commwarrior.Q executable is executed it will copy itself to C:\System\Libs\cw.exe and will create a bootstrap file to C:\System\Recogs\cw3rec.mdl. If a memory card is present, the same files are created also to the memory card.
Commwarrior.Q creates a bitmap file with the name used by the current operator into C:\system\Apps\Phone\oplogo\
This bitmap file (below) is shown instead of the operator logo when the phone is on the network.

The worm then creates SIS files for distributing to other, Bluetooth-discoverable devices. SIS files created by Commwarrior.Q are randomly named and have a random size between 32100 and 32200 bytes.
The filenames are composed of three component string arrays that are stored in the main binary in obfuscated form. The string arrays are:
- smart, nokia, symbian, nice, fatal, cool, c00l, virtual, final, safe, abstract, static, zend, jedi, trend, micro, mega, hard, nice, good,lost
- www, web, wap, email, mail, game, graphics, java, hood, sex, max, audio, memory, RAM, ROM, HDD, WinAmp, jedi, hardware, display, keyboard, key
- antivirus, anti-virus, guard, fucker, hacker, cracker, checker, driver, manager, uninstaller, remover, engine, tool, machine, box, stuff, videoplayer, player, trust, ringtone, explorer, timer, game, AppMan, recorder, dictaphone, team, images, calculator, objects, documents, clips, docs
Activity
When Commwarrior.Q is active on the phone it will create and randomly display an HTML page with the phone's web browser.
The HTML page contains the following text:
Introduction Surprise! Your phone infected by CommWarrior worm v3.0. Matrix has you, CommWarrior inside. No panic please, is it very interesting to have mobile virus at own phone. This worm does not bring any harm to your phone and your significant data. About CommWarrior worm for Nokia Series60 provides automatic real-time protection against harmful Anti-Virus content. CommWarrior is free software and is distributed in the hope that it will be useful, without any warranty. Thank you for using CommWarrior. CommWarrior © 2005-2006 by e10d0r
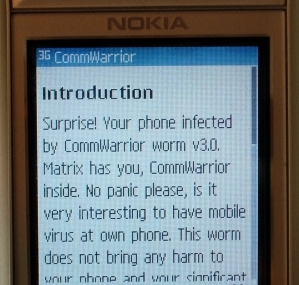
The HTML page is created into directory C:\system\Libs\cwinfo.html
Propagation (Bluetooth)
Comwarrior.Q replicates over Bluetooth in SIS files that have a random name, for example, anyrah5y.sis or xyr88b0muh7.sis.
The SIS file contains the worm's main executable and is located in either C:\ drive or a randomly named directory. It also contains autostart settings that will automatically execute Commwarrior.Q after the SIS file is installed.
On execution, Commwarrior starts looking for other Bluetooth-discoverable devices, and sends a copy of itself to each discoverable device, targeting several in one attempt. The Comwarrior worm will constantly look for new targets, thus it is able to contact all phones in range.
Unlike the Cabir worm, which locks onto one phone as long as it is in range, if a target phone goes out of range or rejects the file transfer, Commwarrior will search for another phone.
Propagation (MMS)
Commwarrior.Q uses three strategies for spreading over MMS messages. On execution, the worm can:
- Go through the phone's address book and send MMS messages to phone numbers that are marked as a mobile phone.
- Reply to any incoming SMS or MMS messages with an MMS message containing the Commwarrior.Q SIS file.
- Listen for any SMS messages being sent by the user and send an MMS message to the same number, right after the SMS message.
The texts in MMS messages sent by Commwarrior.Q contain texts that are stored in the phone Messaging Inbox, thus creating the impression that the recipient is receiving text that is really from the sender.
Propagation (MMC Card)
Commwarrior.Q "listens" for any MMC cards to be inserted into the infected phone, and copies itself to the inserted card.
The infected card contains both the Commwarrior executable and the bootstrap component, so that if the infected card is inserted into another device, the device will also be infected.
Propagation (SIS Files)
Commwarrior.Q searches the C: drive and memory cards for SIS installation files, and will infect all SIS files that it finds. The infected SIS files will be wrapped by Commwarrior.Q so that if the user installs the infected SIS file, Commwarrior.Q will install first followed by the original application.
Infected SIS file will retain the orignal product name so that user will not notice that the SIS package is infected with Commwarrior.Q when installing it.