Net-Worm:W32/Santy
Summary
Santy is a worm was found at December 21st, 2004. It uses a vulnerability in popular phpBB discussion forum software to spread and it uses Google search engine to find vulnerable servers. It does not infect end user computers. Google has started filtering requests made by the worm at December 22nd, 2004, in order to stop the worm.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The worm is written in Perl scripting language. When executed, the worm uses the Google search engine to look for hosts that have phpBB software in use. It does this by searching URLs that contain string "viewtopic.php". In order to get different results with different searches, the worm uses a random string in the search as well.
After the search has been performed, the worm parses the resulting page and attempts to exploit a vulnerability in phpBB software. This vulnerability, known as Highlight Vulnerability, can be used to execute arbitary code on the server running vulnerable version of phpBB. Further information about the vulnarbility is available from phpBB web site at: http://www.phpbb.com/phpBB/viewtopic.php?t=240513
If the worm is able to exploit the vulnerablity, it will attempt to transfer itself to the victim host in 20-byte chunks. If any of the chunks is lost during the transfer, it will cause the worm to get corrupted, which can render the worm disfunctional on the victim. The worm is written to a file "m1ho2of" on the victim. After the transfer is complete, the worm will use the exploit once again to execute the code using the system default Perl interpreter.
Santy contains also a generation counter that is increased every time the worm is executed, i.e. once per infected host. If the number of generations is higher than three (3), it will execute its payload. The payload attempts to replace all files with the following extensions ".htm", ".php", ".asp", ".shtm", ".jsp" and ".phtm".
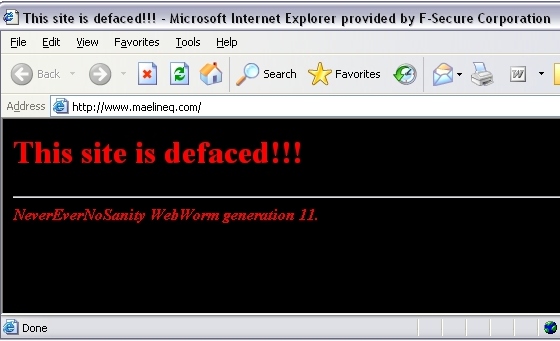
The result is the these files are replaced with a HTML page that contains the following text:
This site is defaced!!! NeverEverNoSanity WebWorm generation X ...
where X keeps growing from one infection to another. The effect is that all replaced pages on the infected sites look like this: