Irok
Summary
Irok is a virus-worm created by RaiD/SLAM which spreads via IRC and Microsoft Outlook. The worm is 10001 bytes long DOS-based program that is heavily packed and encrypted with a protective envelope that uses anti-debugging tricks.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
When run, the worm copies itself to C:\Windows\System\ and C:\Mirc\ folders as IROK.EXE and drops WINRDE.DLL to the \Windows\System\ folder. This file is not a Windows DLL, it is a data file. The worm also replaces SCRIPT.INI file in the C:\Mirc\ folder with its own script that sends the IROK.EXE file to everyone on the IRC channel to which the infected user joins. The worm finally drops a Visual Basic script file IROKRUN.VBS to the Windows Startup directory. This script will be executed next time the system is restarted.
During the next Windows startup, the IROKRUN.VBS script will be executed. It uses Microsoft Outlook to send the worm executable as IROK.EXE to 60 recipients whose addresses are taken from each of Outlook's address books.
The message in which the worm spreads itself looks like this:
Subject: I thought you might like to see this. Body: I thought you might like this. I got it from paramount pictures website. It's a startrek screen saver.
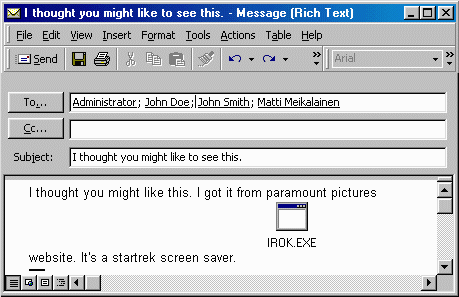
After every message is sent they are removed from the 'Sent Items' folder. Finally the script file is removed from the Windows Startup directory.
At the same time Irok is a non-resident virus, which scans directories listed in PATH= variable for COM and EXE files and then infects them. The virus is a very fast infector. It can infect up to 80 files at a time. The virus is relocating type - it writes itself to the start of the file and relocates the original 10kb of the file to the end. The relocated part is encrypted. Infected files grow 10kb in size.
In some cases the virus can corrupt host programs. The virus has a bug and it does not supply command line options to the host program correctly, so every program that operates with command line parameters will work incorrectly after infection.
The virus avoids infecting files that have extensions and/or their names start with one of the following:
dll spa man drv scr krnl 386 msc com exp mou gw go sta use gdi con
The virus also deletes the following files:
anti-vir.dat chklist.ms chklist.cps vs.vsn ivb.ntz
When internal counters of the virus reach certain values, the virus displays a message on the screen. Most of this message is taken from lyrics of the song 'Aenema' by the band called 'Tool'. We will not reproduce the message here as the song seriously needs the Parental Advisory sticker for explicit lyrics.
The message ends with this text:
... People cry and people moan. look for a dry place to call their own, look for a dry place to rest there bones. Thanks for reading the text above, I've had enough time to remove the contents of your hard disk for you. :-) IRoK v1.1 - RaiD/SLAM[2000]
And indeed, the virus has corrupted files on the hard drive during this event.
The virus also has several internal text strings:
IRoK v1.1 is initializing... Ok! Hey You! <----------- >>> Push enter stupid! RaiD/SLAM[2000]
The Irok virus-worm will not spread itself via Outlook if Windows Scripting Host is not installed on the infected system. The worm will not work if Windows is installed in some other directory than C:\Windows\ and it will not spread itself via IRC if mIRC is installed in a directory other than C:\Mirc\. Regardless of software installed, the worm will infect COM and EXE files on the system it infects.