Email-Worm:W32/Zhelatin.CT
Summary
The Zhelatin.CT worm started to spread on April 13th, 2007. The worm spreads in emails with love-related subjects and with attachments named "Love Card.exe", "Greeting Card.exe" and so on. A bit later the same variant spread using security-related subjects.
Removal
Based on the settings of your F-Secure security product, it will either move the file to the quarantine where it cannot spread or cause harm, or remove it.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
The functionality of the Zhelatin.CT worm variant is similar to Zhelatin.CQ , however the subjects and attachment names it uses are different.
On April 13th several emails with love themed subjects were seen in the wild. While some of the subjects are a rehash of previously used subjects such as Sending You My Love, The Dance of Love, and When I'm With You, others are new:
- A Dream is a Wish
- A Is For Attitude
- Eternal Love
- Eternity of Your Love
- Falling In Love with You
- Hugging My Pillow
- Inside My Heart
- Kisses Through email
- Our Journey
- Sent with Love
- When Love Comes Knocking
- You're In My Thoughts
- You're the One
The email messages themselves have no text, instead, they have attached executables with romantic sounding filenames. These include:
- Love Card.exe
- Love Postcard.exe
- Greeting Card.exe
- Postcard.exe
Here is an example of the worm's email:
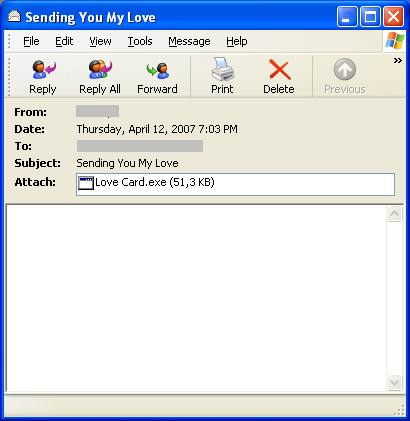
A second run occurred after a few hours. This time, the subjects were security related:
- ATTN!
- Spyware Alert!
- Virus Alert!
- Worm Alert!
- Worm Detected!
Furthermore, the message body is an image file which advises the receiver to patch their systems. Also included within the image is a password in order to extract the attachment. Here is an example:
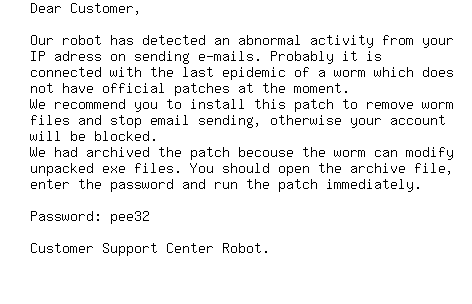
Something new to the Zhelatin family is the use of a password protected Zip archive as an attachment. The filenames vary but they have the following format:
- patch-[4 to 5 random numerical characters].zip
- hotfix-[4 to 5 random numerical characters].zip
The executable contained within the Zip archive has the same name as that of the archive but with an EXE extension.