Summary
CSC/CSV is the first Corel Script virus.
Corel Script is the built-in script language of several Corel applications, including Corel Draw. These scripts are stored in plain text files with extension "*.csc".
Removal
Based on the settings of your F-Secure security program, it will either automatically delete, quarantine or rename the detected program or file, or ask you for a desired action.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
Variant:CSV.A
CSC/CSV.A is a quite simple prepending virus and the virus attempts to infect all files that have extension "*.csc" from current directory when an infected script is executed.
Before the virus attempts to infect the file, it checks if the file is already infected. It tests if the first line of the file starts with the following text:
REM ViRUS
If this text does not exist, the virus first renames the target file to "mallorn.tmp". Then it creates a new file using the name of target file. Next it copies itself to this new file and finally appends the contents of the "mallron.tmp" to the end of the file.
After this has been done, the virus will delete the "mallorn.tmp" file, and proceed to the next file.
The payload is supposed to activate at June 6th. However, the activation depends of the current date format settings in the Control Panel and it fails with certain settings. If the payload activates, then it will show the following message box:
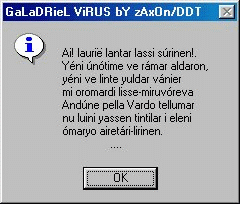
The message is taken from the book "Lord of the Rings" written by J.R.R. Tolkien. It is a part of "Galadriel's Song of Eldamar" and it is written in the language of High Elves.
English translation of the text above is as follows:
Ah! like gold fall the leaves in the wind, long years numberless
as the wings of trees! The long years have passed like swift
draughts of the sweet mead in lofty halls beyond the West, beneath
the blue vaults of Varda wherein the stars tremble in the song of
her voice, holy and queenly.
If the virus infects the built-in scripts of Corel Draw, it causes that some of these scripts will no longer work. Instead they give the following Corel Script error message:
Script <script name> contains an error and could not be run.