SpywareSheriff
Summary
SpywareSheriff is an rogue antispyware application that uses false and/or misleading scan results and questionable interface design to push the user into purchasing a license.
Removal
Based on the settings of your F-Secure security product, it may block the file from running, move it to the quarantine where it cannot spread or cause harm, or ask you to select an action.
A False Positive is when a file is incorrectly detected as harmful, usually because its code or behavior resembles known harmful programs. A False Positive will usually be fixed in a subsequent database update without any action needed on your part. If you wish, you may also:
-
Check for the latest database updates
First check if your F-Secure security program is using the latest updates, then try scanning the file again.
-
Submit a sample
After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis.
Note: If the file was moved to quarantine, you need to collect the file from quarantine before you can submit it.
-
Exclude a file from further scanning
If you are certain that the file is safe and want to continue using it, you can exclude it from further scanning by the F-Secure security product.
Note: You need administrative rights to change the settings.
Technical Details
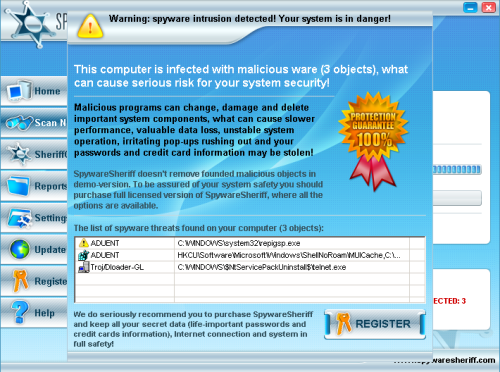
Once installed, SpywareSheriff starts automatically during the boot process and performs a scan for spyware. The only simple way to close the application is to register for the license, and the license is required for any cleaning of supposedly detected malware.
In some cases, Spywaresheriff is advertised by a trojan with a hoax message that the system is unsafe. The trojan malware does not install the antispyware application. If the user clicks on the warning message, they are directed to a website from which the user can download and install SpywareSheriff.
Please note: it is possible to find, download and install this application without being pushed by a trojan. Search engine results can also lead to the discovery of spywaresheriff.com and a user can decide to install it on their own. The scan results however, will still contain false positives. See below for further details.
The SpywareSheriff antispyware application itself is not necessarily harmful to the user's computer.
Screenshot of trojan malware, detected as not-virus:Hoax.Win32.VB.l, generating a message that the system is unsafe:
Clicking on the message displayed above will open the computer's web browser to a page from which SpywareSheriff can be downloaded.
Screenshots of SpywareSheriff presenting a false detection:
.png)
The message above was generated on a previously clean system image. Note that the third item listed is telnet.exe, a Microsoft application installed with the Windows Operating System. The first and second items listed in this example are the trojan malware referred to above.